Cyber Security Threat Types We Circumvent and/or Neutralize
Promotion: Pen Testing Starting $25.00/hr
Attack Solutions, Inc.
A Global Leader In Cyber Security Services
Cyberattacks have grown exponentially over the last few years and since the spread of Covid-19 organizations have experienced a threefold increase in cybercrimes. Attack Solutions, Inc. (ASI) has responded to this increased demand by expanding its human capital of cyber experts, transformed its cyber operational practices, and embraced advance technologies to better confront the security challenges presently inundating organizations. ASI works preemptively with businesses to detect, neutralize, and prevent known threats, and implements robust cyber policies so that businesses are less vulnerable to innovative exploits. We have evolved to become experts at conducting ethical mock attacks against enterprise networks applying some of the most innovative techniques and technologies in penetration testing, network intrusion, and vulnerability exploitation.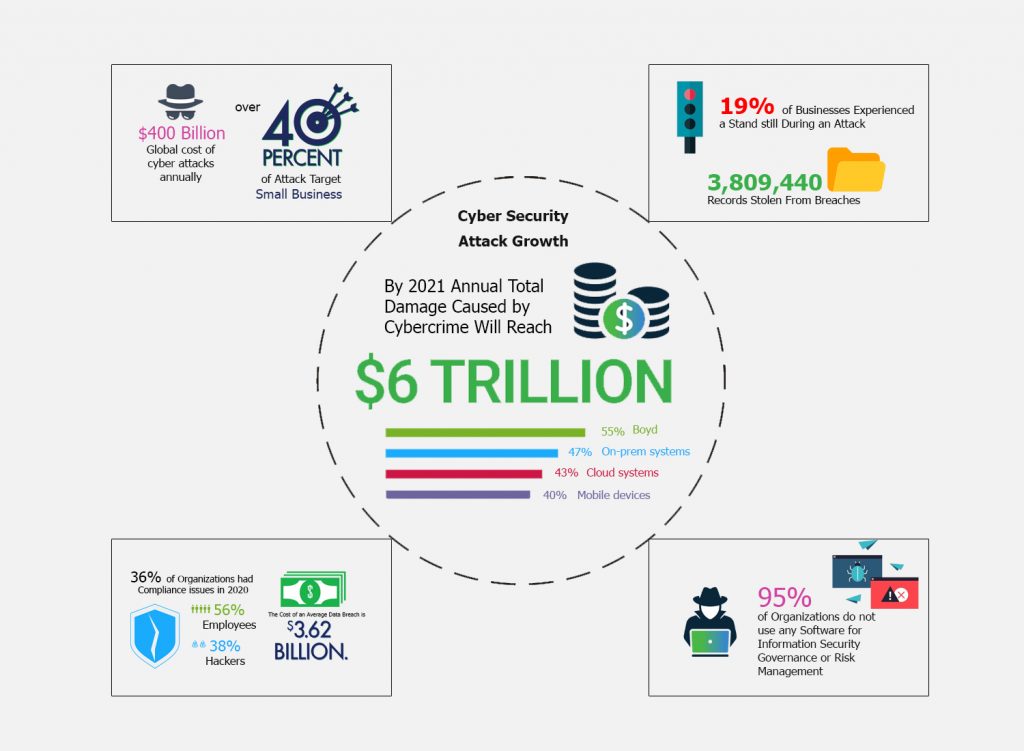 ASI empowers organizations to elevate their security posture through the vigilant execution of ethical mock attacks revealing hidden vulnerabilities and recommending remediation and neutralization approaches. By applying real time analytics, artificial intelligence, and machine learning we baseline global cyber security trends to evolve and adapt potent cyber circumvention remedies to neutralize newer exploit types. Our professional network of global cyber security practitioners and expert ethical hackers become your roster of cyber allies in conducting pen testing cycles, hardening systems, and formulating and implementing robust security policies. ASI has instituted a cyber rapid response team that can be engaged in a moment’s notice to jointly function with your team to circumvent active exploits before penetration and damage can reach an unrecoverable state.
ASI empowers organizations to elevate their security posture through the vigilant execution of ethical mock attacks revealing hidden vulnerabilities and recommending remediation and neutralization approaches. By applying real time analytics, artificial intelligence, and machine learning we baseline global cyber security trends to evolve and adapt potent cyber circumvention remedies to neutralize newer exploit types. Our professional network of global cyber security practitioners and expert ethical hackers become your roster of cyber allies in conducting pen testing cycles, hardening systems, and formulating and implementing robust security policies. ASI has instituted a cyber rapid response team that can be engaged in a moment’s notice to jointly function with your team to circumvent active exploits before penetration and damage can reach an unrecoverable state.Recent Attacks
Ivanti has rolled out security updates to address two security flaws impacting Ivanti Endpoint Manager Mobile (EPMM) that have been exploited in zero-day attacks, one of which has been added… [...]
A new joint investigation by SentinelOne SentinelLABS, and Censys has revealed that the open-source artificial intelligence (AI) deployment has created a vast "unmanaged, publicly accessible layer of AI compute infrastructure"… [...]
This week’s updates show how small changes can create real problems. Not loud incidents, but quiet shifts that are easy to miss until they add up. The kind that affects… [...]
A study by OMICRON has revealed widespread cybersecurity gaps in the operational technology (OT) networks of substations, power plants, and control centers worldwide. Drawing on data from more than 100… [...]
Beyond the direct impact of cyberattacks, enterprises suffer from a secondary but potentially even more costly risk: operational downtime, any amount of which translates into very real damage. That’s why… [...]
Recent Announcements
RSS Error: A feed could not be found at `https://www.darknet.org.uk/feed/`; the status code is `429` and content-type is `text/html; charset=UTF-8`

Get a Quote
If you have questions or comments, please use this form to reach us, and you will receive a response within one business day. Your can also call us directly at any of our global offices.